Why cross-chain interoperability matters right now

If you’ve used more than one blockchain, you’ve probably felt the pain: assets stuck on one chain, liquidity fragmented across networks, and clunky bridges that feel risky. That’s exactly the gap cross-chain interoperability tries to close. Instead of treating each blockchain as an island, we want a web of networks where value, data and logic move smoothly. For DeFi, NFTs, gaming and institutional settlement this is no longer a “nice to have”, it’s a survival requirement. The trick is doing it without blowing up security, compliance or user experience in the process.
Step 1: Understand what “interoperability” actually means
Interoperability is not just “moving tokens between chains”. At a deeper level, it’s about three things: asset transfer, data messaging and shared execution. Asset transfer is the classic bridge use case. Data messaging lets one chain react to events on another, like liquidations or oracle updates. Shared execution means smart contracts on different networks coordinating like microservices. Most cross chain interoperability solutions for blockchain try to cover at least two of these layers, but very few do all three well, which is where careful design and trade‑offs come in.
Key components you should know
Under the hood, nearly every cross-chain setup depends on four building blocks: messaging layer, verification layer, liquidity layer and application logic. The messaging layer transports information between chains; the verification layer proves that a message is genuine; the liquidity layer ensures there’s something to move; and the app logic decides what to do once a message is trusted. When people argue about which is the best cross chain interoperability protocol for defi, they’re usually disagreeing about how to design these pieces, especially who verifies messages and how liquidity gets managed.
Step 2: Learn the main technical approaches
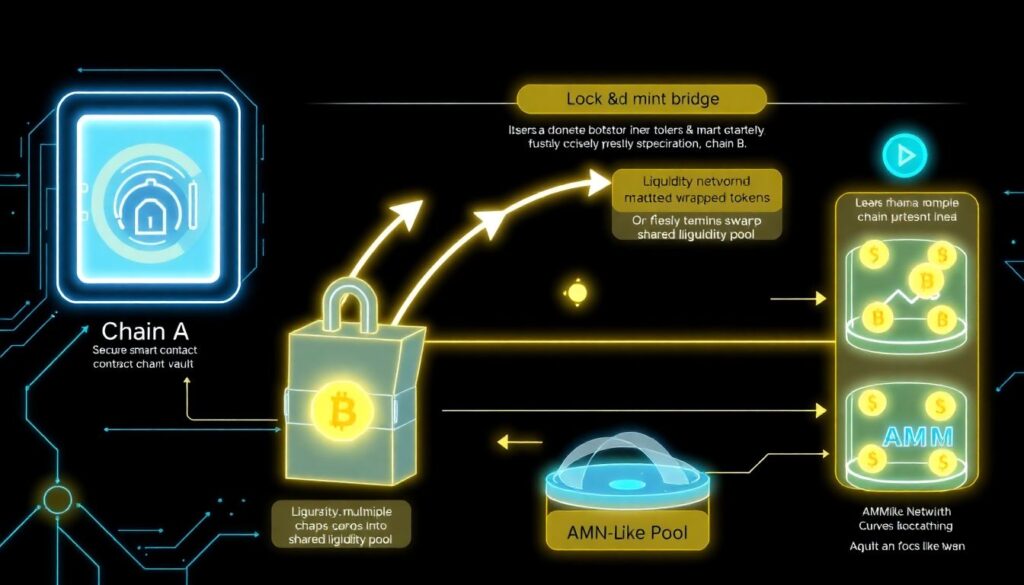
To make sense of the landscape, it helps to group solutions into a few patterns. First, lock‑and‑mint bridges: you lock tokens on chain A, mint wrapped tokens on chain B, and reverse later. Second, liquidity networks and routers: users swap into pooled liquidity, often via AMM‑like designs, instead of creating wrapped assets. Third, light‑client‑based protocols: they run a lightweight node of one chain on another to verify proofs directly. Fourth, shared or modular security setups, where a third chain or committee handles verification for others, trying to balance trust and decentralisation.
How bridges actually move your assets
In typical bridges, a smart contract on the source chain locks your token and emits an event. Off‑chain relayers or a validator set watch for that event, then trigger a mint or release on the destination chain. If verification is weak or the validator set is compromised, attackers can mint unbacked assets, which is why bridge hacks have been so catastrophic. Secure cross chain bridge development services now emphasise stronger validation, better key management and formal verification of contracts, because the “weakest link” problem is brutal when billions in value sit behind one contract.
Step 3: Recognize the main challenges
The first and biggest challenge is security. Interoperability adds complexity, and complexity tends to create bugs and attack surfaces. Each new connection between chains effectively multiplies risk, since a flaw in one component can cascade. The second is consensus mismatch: different chains use different finality assumptions and latency, making it tricky to know when it’s truly safe to act on a cross‑chain message. Third, UX fragmentation: users juggle networks, fees, token formats and wallet permissions, which makes even simple transfers feel intimidating, especially for people new to crypto.
Economic and governance pitfalls
Even if the tech works, the economics can fail. Liquidity has to be deep enough on both sides, or users face high slippage and delays. Incentive misalignment between validators, liquidity providers and protocol governors can encourage risky behaviour, like over‑optimistic security assumptions to chase volume. Governance is another landmine: who gets to upgrade the bridge, pause it under attack, or change fee models? Enterprise cross chain bridge platform operators often centralise these levers for reliability, but that reintroduces trust and regulatory exposure, which community projects usually try to avoid or at least minimise.
Step 4: Learn from common mistakes (and avoid them)
New teams often treat a bridge as “just another smart contract”, underestimating how adversaries target it. Skipping independent audits, re‑using unproven code and ignoring adversarial testing are classic errors. Another mistake is building custom message formats without clear standards, which makes integration painful for wallets and dApps. On the user side, people blindly trust any bridge with a nice UI, not checking whether it’s audited, battle‑tested or even permissionless. Focusing only on low fees while ignoring security history is a quick way to become part of the next headline exploit.
Security warnings you shouldn’t ignore
If a bridge relies on a small multisig, note that you’re effectively trusting a handful of keys with all locked funds; social engineering or key theft can be enough to drain everything. Over‑complex token wrapping, with multiple layers of synthetic assets, compounds risk because each hop is a potential failure point. Beware of protocols that hide or obfuscate validator sets and governance rules; transparency is a baseline requirement. Finally, remember that on‑chain bugs and off‑chain infrastructure issues, like compromised relayers, are equally dangerous in an interconnected cross‑chain system.
Step 5: Choose the right interoperability model
For DeFi protocols, the priority is often atomicity and composability: you want cross‑chain operations that feel as close as possible to a single transaction. That pushes you towards protocols with strong on‑chain verification, like light‑client or zk‑based systems, even if they’re more complex to implement. Retail‑focused wallets, in contrast, might choose liquidity routers that prioritise speed and UX. Institutions and exchanges often pick an enterprise cross chain bridge platform that offers SLAs, compliance hooks and operational support, accepting some centralisation in exchange for predictable behaviour and clear responsibility.
Matching tools to use cases
If you’re building a DEX that must route across chains, look at cross chain interoperability tools for crypto exchanges that expose clean APIs, monitoring dashboards and risk controls. For NFT games, simple lock‑and‑mint or burn‑and‑mint flows might be enough, especially if asset values are modest. For lending protocols, where collateral safety is everything, you want verifiable cross‑chain oracles and robust message verification first, fancy UX later. Resist the urge to adopt flashy architectures just because competitors do; align your interoperability layer tightly with your threat model and business priorities.
Step 6: Practical tips for beginners
If you’re a developer starting out, begin in a testnet sandbox. First, integrate a well‑known bridging SDK, move small test assets, and instrument everything: logs, events, and error paths. Second, read past post‑mortems of bridge hacks to understand how real attacks unfolded; this sharpens your intuition more than docs alone. Third, bring in external auditors early, even informally, to challenge your assumptions. If you’re a user, start with official bridges or those recommended by reputable wallets, and never move an amount you can’t afford to lose in a single transaction.
Expert recommendations on best practices
Security engineers who specialise in bridges consistently recommend a “minimum trust surface” approach: move verification on‑chain where possible, use battle‑tested cryptographic primitives and avoid bespoke crypto. They also push for strong monitoring: real‑time anomaly detection on locked balances, validator behaviour and message patterns. Architects evaluating the best cross chain interoperability protocol for defi emphasise modularity: keep messaging, verification and liquidity layers separable, so you can swap components as technology advances. Finally, experienced product teams stress education—clear warnings in the UI and honest risk disclosures reduce both user harm and reputational damage.
Step 7: Building and operating secure cross‑chain systems
Once you move from prototype to production, process matters as much as code. Set explicit security budgets, enforce multiple independent audits, and run recurring chaos tests that simulate validator failures and delayed messages. Define incident response playbooks: who can pause the bridge, under what conditions, and how to communicate with users. Maintain conservative limits on transferred value initially, then raise caps as the system proves itself. Treat every upgrade as a potential new system, subject to full regression testing, because subtle changes in verification or fee logic can have unexpected security consequences.
Where cross‑chain is heading next
The future likely looks less like isolated bridges and more like interoperability layers becoming part of core infrastructure: rollup interoperability hubs, shared security networks and native cross‑chain messaging baked into L1s. Zero‑knowledge proofs should gradually make light‑client‑style verification cheaper and more flexible. For builders, that means planning for migration: design contracts and governance so you can adopt better interoperability rails later without breaking users. For users, it means being cautious during transitions, as “next‑gen” systems will be heavily targeted until their security assumptions are proven in the wild.